
School of Electrical and Computer Engineering
What is Hacking?
According to Wikipedia, the original term of “Hacking” means to express admiration for the work of a skilled software developer. However, some frown upon using ‘hacking’ as a synonym for security cracking - in distinct contrast to the larger word, in which the word hacker is typically used to describe someone who “hacks into” a system by evading or disabling security measures. Nowadays, ‘hacking’ is more widely used than ‘cracking’.
An On-line Environment Vulnerable to Hacking
Thanks to the development of the Internet, almost anything has become possible on-line, especially in the past few years. These days we are able to shop, create our own blog, chat on-line with others, download necessary data, and so on.
An on-line shopping mall allows us to buy products just like we did off-line for decades. Especially for clothes, now we can shop from various choices compared to real department store, and order them through the website. For modern people like us, who live hectic lives, this improvement in technology has made it possible both ordering and receiving products at home. Although we cannot actually try on the clothes before we buy them, we can predict ourselves wearing clothes we have chosen through photographs of clothes in their life-size. Also, we can get useful information from comments that other customers have written. The delivery is usually within 1~3 days, and refunds and exchanges are available when there is a problem on the product. This convenience in buying clothes is also applicable to other products such as cosmetics, furniture, foods, and so on. One click of a computer mouse is substituting all the money and time spent on going to look for and buy things.
We, human beings, are social animals and therefore require close relationships with other people. Every day we meet various people and create or maintain relationships. Unfortunately, it is not possible for us to personally meet all the people we know as each of us has our own work and life. Therefore, SNSs have been created in order to make our life and relationships more efficient. These days, we are able to let others know how we are getting along through SNSs like Cyworld, Micro Blogs, Nate-On, Twitter, and so forth. Most of you would probably have an experience of doing group assignments late at night through the instant messenger program called ‘Nate-On’.
Recently, a daily used cellular phone has been upgraded into a smartphone. This device has allowed people to do their work when they are moving, even making financial services available. As we download the necessary applications from the website, we can access the Internet through this one portable device!
Like shown above, we can enjoy a much more convenient life through the Internet and the improvement in science technology. However, this can also mean all the devices we use could be a passage where viruses and spywares of every kind can enter and hack our devices. Hacking not only paralyzes computer systems but can also cause an invasion of privacy and even financial damage by leaking personal data.
Damages Caused by Hacking
We are defenselessly exposed to the damages of hacking, from individuals to national institutions.
To begin with the narrow limits, there is a danger of leaking of personal data. Do you remember the big accident of the website ‘Auction’ in 2008? At that time, personal information of about 10,810,000 customers had been disclosed. After this massive incident, other management companies with excessive members (from shopping sites to portal sites) have strained themselves in preventing information leaks. They enhanced security by improving apparatus for implementing spam filtering service and offering members download hacking prevention programs. However, various incidents have occurred since early last year. In April 2009, about 90,000 members’ IDs and passwords were exposed and in the same year in July, customers’ 8 electronic money (e-money) was extorted from the Auction site. In August 2009, IDs and milege of the on-line shopping mall G-market members had been used in sending 2,100 spam massages advertising gambling sites. On March 2010, 25 enterprises including ‘Sinsegae Mall’ and ‘I-Love-School’ websites had leaked approximately 20 million customers’ personal information.
Personal information leaks can cause trivial inconvenience like spam messages sent to numbers disclosed but even worse, you can become a delinquent borrower by the groups of people who illegally take out loans. They make 9 Dae-po Phones (大砲 Phone, a phone opened with the name of a different person) and borrow money from financial companies using customers’ information.
The most apprehensive thing that should be concerned is one’s social security number. This is because your social security number is not changeable while your ID and password can be changed. To solve this problem, the government is planning to make the use of an i-PIN mandatory from 2015. When an i-PIN number is issued through six institutions including Seoul Credit Rating & Information Inc., there would be no need to insert your social security number when joining another website. Therefore, the government considers the use of it would prevent information leaks from hacking. However, a weak spot of this i-PIN policy has been revealed. Cyber Terror Response Center arrested a group of men who illegally issued i-PIN numbers using disclosed social security numbers and sold them to online game suppliers in China. They attempted to hack by seeking flaws in the security process in confirming identities. Therefore, Korea Communications Commission (KCC) immediately stopped the utilization of 4,700 i-PIN numbers that were possibly issued illegally. They also took measures to exclude unregistered prepaid cards in the identification process. However, the problem is that it is difficult to ultimately prevent illegal i-PIN issues because it is easy to get i-PIN numbers using social security numbers that have already been leaked. What is even worse is that there is no way to assume how many social security numbers have been disclosed. This implies that the security of introducing an I-PIN policy is not perfect.
|
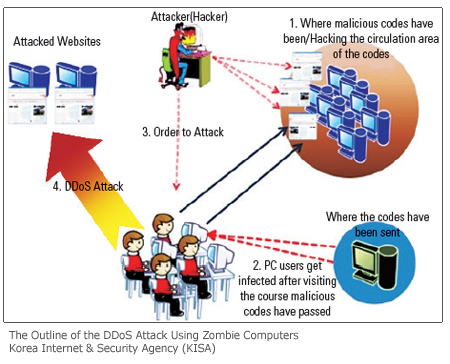
DDoS Attack is a more serious problem. Though it has been a year since the DDos Crisis happened, a lack of improvements is being made. Recently, Researcher Ahn (Ahn Chul-soo, the chairman of the AhnLab Inc.) announced the problem of hacking into SNSs as one of the 12 security issues of the year. In fact, The Department of Justice, City of Seoul, and one of the famous Korean portal websites NAVER have been attacked by DDoS. While DDoS attacks were mainly focused on specific institutes in the past, now these attacks have little regard to any objectives and will attack game sites, online shopping malls, financial companies, and so on. Malignant codes are being widely distributed through SNSs these days.
Approximately 280 new malignant codes have been created in a year and there are recently about 30 DDoS attacks per day. But this cyber attack is not the only problem. According to the Cyber Terror Response Center, personal information taken away from zombie computers used in the process of an attack has even been disclosed to other countries. Individual data including the names of recently written files to a list of recently visited websites are saved in those computers. The police say that the malignant codes executed in zombie computers have leaking information features so that the partial list of saved files would likely be leaked when infected. This data has been released to 59 countries and to servers of 416 computers up until now. A serious financial damage is of concern if personal information, especially your authentication certificate, is leaked.
An invasion of privacy is another problem caused by hacking. As SNSs are widely used these days, members of these systems, especially celebrities, are all influential candidates of being privately invaded. Personal information of famous people is overtly exposed online under the excuse of ‘curiosity about celebrities.’ Therefore, their private areas in networks are often hacked and some hackers even pretend to be those celebrities by loading files or quotes to confuse their fans. Recently, a famous Korean comedian’s pictures were leaked by hackers. This not only violated her portrait rights but also infringed a copyright of the photos since those were for magazines. Unwanted exposure of one’s privacy (such as where they live, photos of the past and so on) can confuse people and let them write abusive comments about those facts. This could make the victims suffer from serious mental anguish and even lead to committing suicide.
Safeguarding Your IT Devices from Viruses
As seen above, the skill of hacking is gradually developing and many of institutions have trouble dealing with it. However, things we believe trivially could be the best effort and a way of preventing our devices from hacking. Listed below are some of the rules we should follow in order to safeguard ourselves from viruses.
|
Byeon In-jin / Yang Chan-sik Reporter / Junior Re
webmaster@uos.ac.kr

